In the previous article, I’ve touched the layer 2 MTU topic. This time, we will see how’s the behaviour of layer 3 MTU in 3 different scenarios.
Packet structure
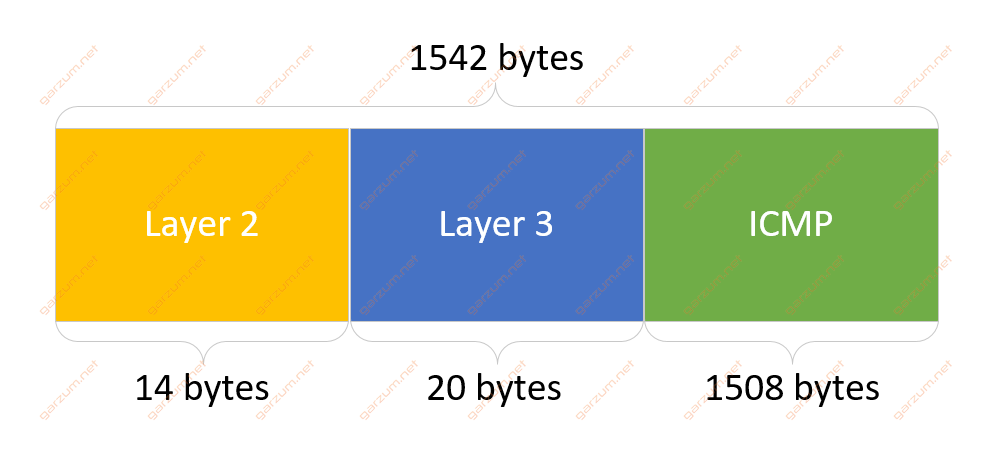
First of all, before we touch on some case scenarios, let’s take a look at the structure of the ICMP packet. The examined packet is a standard ICMP echo request sent by a Linux machine by using a ping command without additional options.
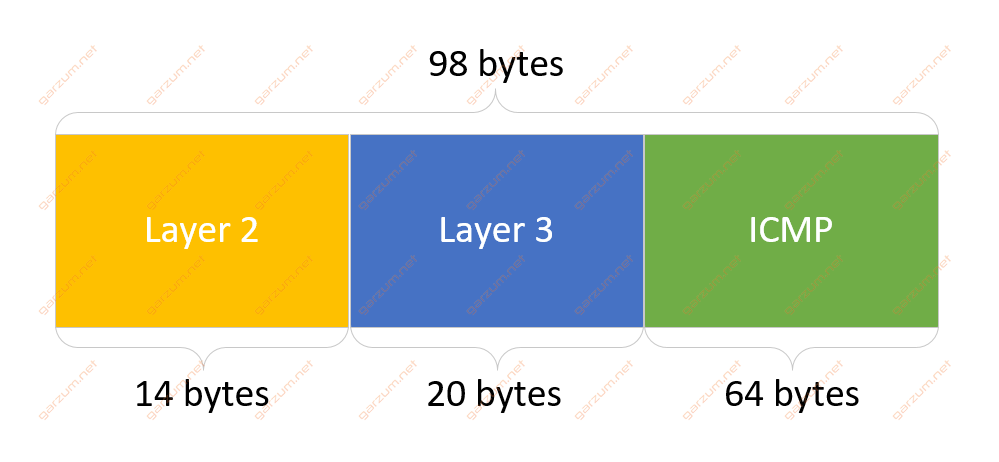
Now since we know what’s a packet structure and the length of particular parts, we can dive deep into case scenarios.
Case scenarios
The topology for all case scenarios is the same. We’ve two Linux PCs interconnected by the Cisco router. There is one Wireshark configured to capture traffic between PC1 and Router. The difference between the scenarios lays in the interface L3 MTU configuration on the router.
Case 1
In this scenario, the Router is configured with standard – 1500 L3 MTU on both interfaces – Gi0/0 and Gi0/1.
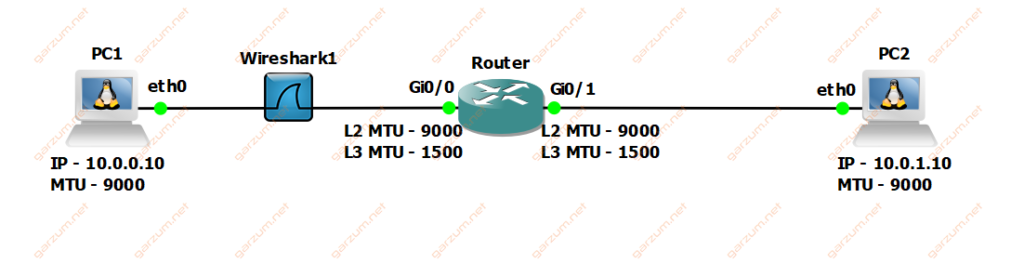
Before we start, let’s check both L2 and L3 MTU configuration of interface Gi0/0.
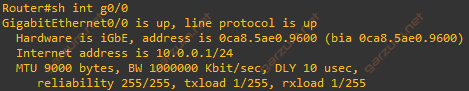
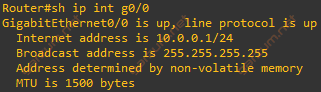
As we can see, the MTU settings are correct.
We will start with the ping command. The packets are 1542 bytes length in total. Here’s the exact packet structure.
To send such packets we will use the ping command with -s option, which allows us to specify packet length.
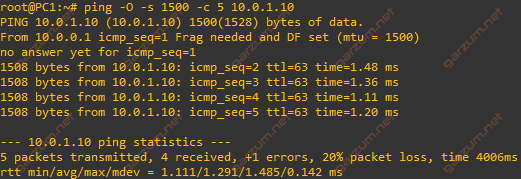
The output indicates, that there is a connection between PC1 and PC2, but we have also received information from the Router(10.0.0.1). It turns out, that packets sent by PC1 are too large, and exceeded the configured L3 MTU. There is also information about the DF flag. DF stands for Don’t fragment. Packets with this flag cannot be fragmented by any network device between sender and receiver. The ICMP echo request packets in Ubuntu by default have this flag set.
Let’s take a look at the captured packets on the Wireshark1.
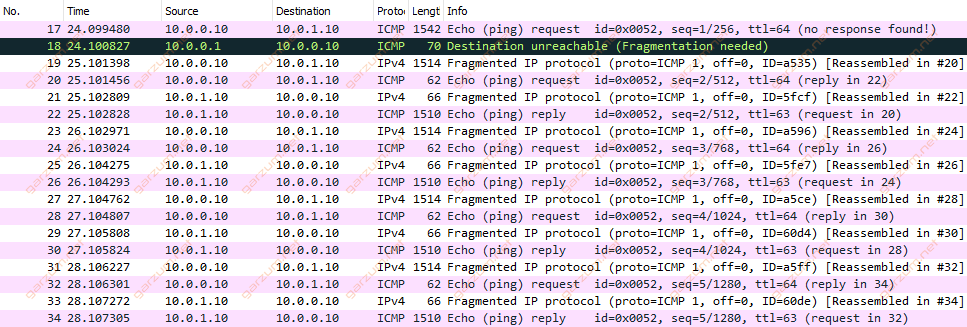
The first packet is a standard ICMP echo request with a length of 1542 bytes, but we’re not getting a response for that packet from PC2. Instead, we’re getting a message from the Router – Destination unreachable (Fragmentation needed).
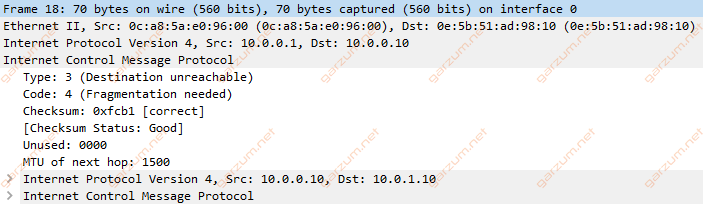
This message informs PC1, that the interface Gi0/0 of the Router is not supporting such large packets, and PC1 should send smaller – fragmented packets.
If you take a closer look at the next packets, you can see, that PC1 adjusted the packet size to the MTU configuration of the Router, and fragmented every large (1542 bytes) packet into two packets (1514 bytes and 62 bytes). Splitting packet like that allows the router to forward them further.
We can do a test with a DF flag. By specifying the -M do option, we’re sending packets without any fragmentation by PC1, and with DF flag set, so the packets cannot be fragmented by any other network device.
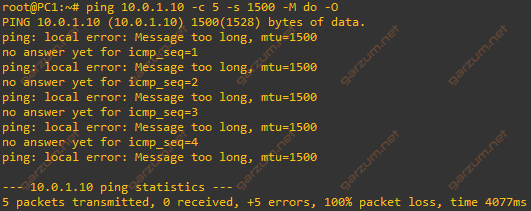
As you can see, PC1 remembers the L3 MTU settings of the Router, and refuses to send such large packets, because the router won’t forward them anyway.
From the output of Wireshark1 we can deduce, that the largest packet, that the router can forward without any fragmentation is 1514 bytes. Let’s check it!
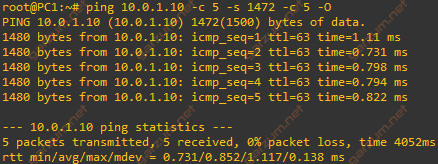
We’ve sent 5 packets with total length of 1514 bytes. Everything seems to be working, let’s check the Wireshark.
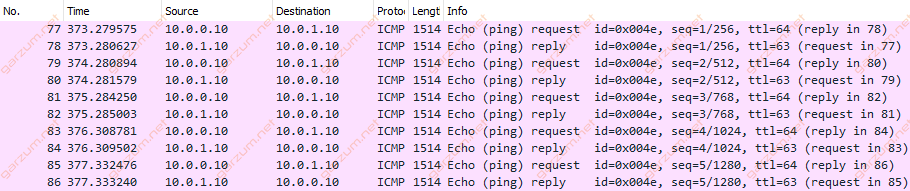
We’ve captured 10 packets. As you can see, there are no fragmented packets.
Let’s now send one byte larger packets – 1515 bytes in total.
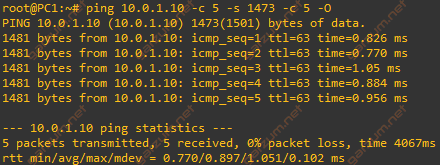
Communication is correct, let’s check the Wireshark.
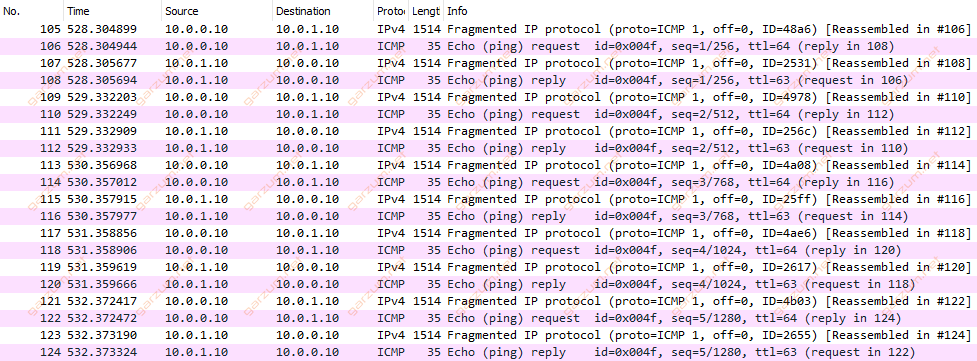
There are fragments. Again we have 1514 bytes length packets – which are a maximum that the router can handle, and the second with 35 bytes = 14 bytes L2 + 20 bytes L3 + 1 byte of the remaining packet.
That leads to the conclusion, that the interface with configured 1500 L3 MTU can forward without fragmentation packets up to 1514 bytes.
Case 2
In this scenario, we will change the L3 MTU on the Gi0/0 interface to 9000. The rest of the topology stays the same.
Let’s check the settings first.
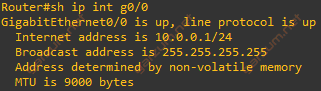
Okay, we’re ready to go. Let’s once again send a packets with total length of 1524 bytes.
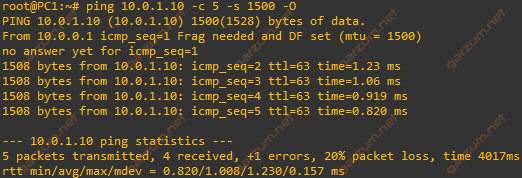
Situation seems to be very similar, but let’s take a look at the Wireshark.
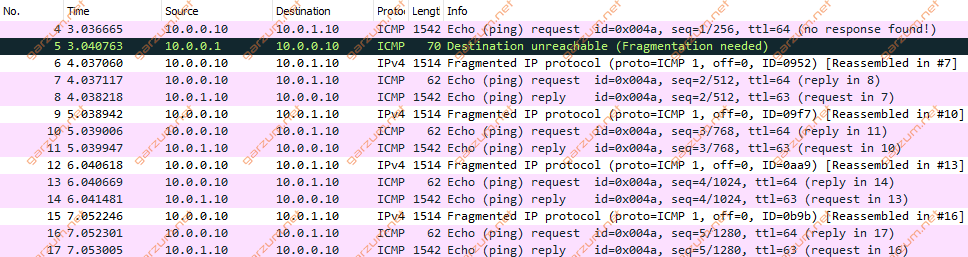
There’s one difference between this, and the previous case. The response – ICMP reply is not fragmented.
Case 3
In the last example, both router interfaces are configured with L3 MTU of 9000.
Let’s send icmp echo request packets with a length of 1542 bytes each.
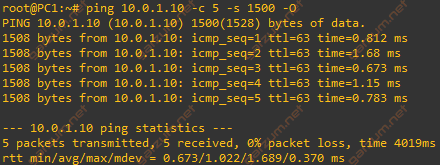
As we can see, for the first time, there is no information about fragmentation. Let’s take a look at the Wireshark output.
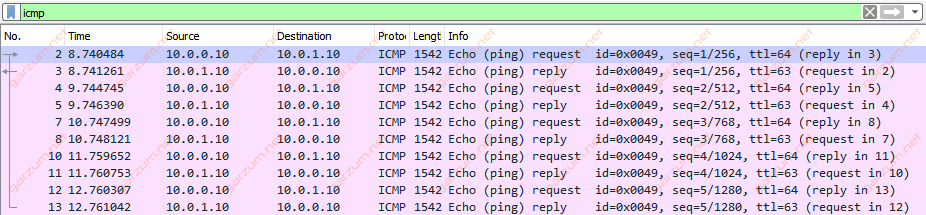
There is no fragmentation in the Wireshark aswell. The packets are forwarded as they are.
